Story
Secure and Resilient "On the Edge" Communication Terminal
Context and Motivation
This project will likely appeal to fans of post-apocalyptic fiction, tech-savvy preppers, and anyone interested in resilient, off-grid communication.
Imagine a world without networks, without Internet, without centralized infrastructure—yet with a vital need to communicate securely and discreetly. This terminal was designed exactly for that. Not to simulate a collapse scenario—but to function in one.

Secure communication is still a major challenge in a world where connected devices—smartphones, laptops, tablets—are obvious targets for increasingly sophisticated attacks. These systems, built on millions of lines of code across OS, drivers, firmware, and applications, expose massive attack surfaces. A single memory management flaw or side-channel access to a GPU can compromise the integrity of a message—even when encryption is used.
The mere use of the Internet reveals sensitive metadata: who is talking to whom, when, and from where. In some cases, raw data packets can even be intercepted and potentially decrypted later. Even well-regarded secure, open-source apps rely on enormous software stacks that are nearly impossible to fully audit.
This project is a response to that reality: a self-contained, network-free, OS-free, app-free device designed with a single, uncompromising goal—to exchange textual and geolocation data in a completely secure, untraceable, and infrastructure-independent way.
Encryption is only a problem when the key is shorter than the message.
Here, it’s the opposite: short messages are protected using long, disposable, time-synchronized keys, drawn from a preloaded sequence that far exceeds the total volume of exchanged data.
Project Goal
This project proves that a well-designed, minimalist embedded system can offer stronger communication security than most modern consumer tech. It enables text and GPS coordinate exchange in offline environments, with high reliability and confidentiality. Thanks to LORA radio, it provides long-range communication, low power consumption, and strong resilience to jamming or interception.
Each message is encrypted using AES-256, with a new key selected every two minutes, synchronized between terminals using either GPS time or an ultra-stable RTC. These keys are stored in sequence on an SD card and are destroyed immediately after use, making post-capture decryption impossible.
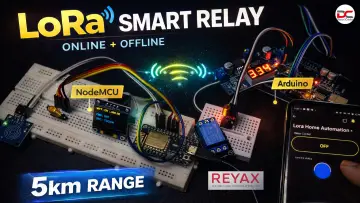
Device Overview
The terminal is built around a Raspberry Pi Pico microcontroller—chosen specifically for its simplicity and lack of opaque or inaccessible subsystems. A 3.5" SPI-connected IPS touchscreen offers a smooth interface for navigating between the message composer, address book, GPS tools, radio setup, and repeater mode.
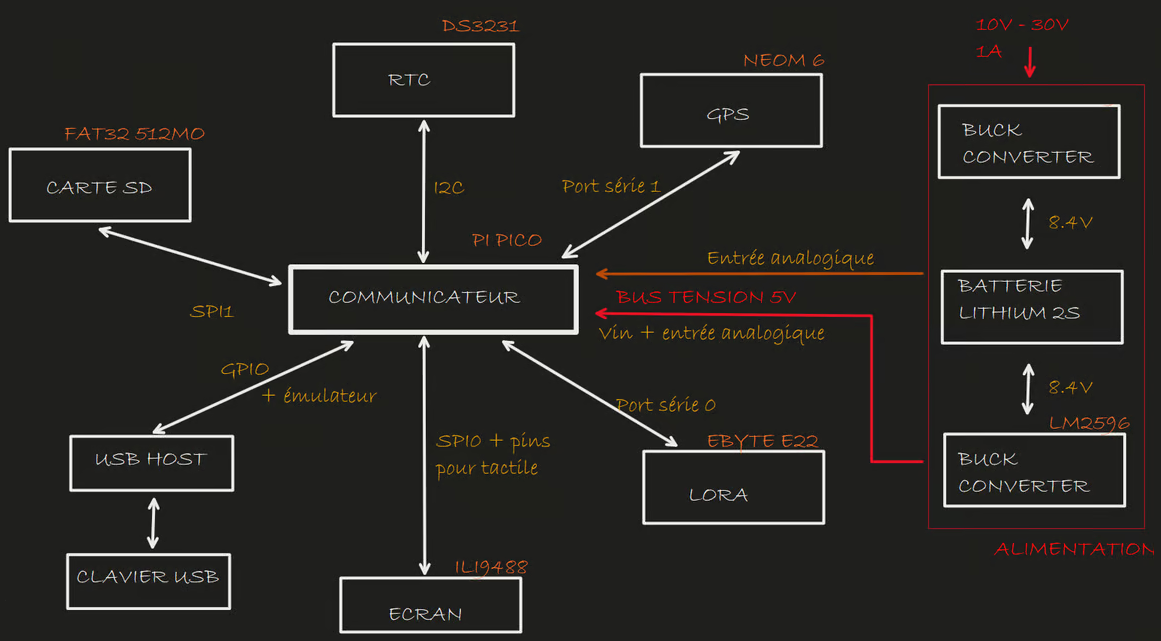
Messages are typed using a standard USB keyboard connected via GPIO-based USB Host emulation—no proprietary chips required. This provides user comfort with a commonly available peripheral while keeping hardware costs and complexity low.
GPS coordinates are provided by a NEO-M6 module. Synchronization is handled by either GPS or a DS3231 real-time clock, which can remain accurate to within seconds for many months without adjustment.
The radio module is a LORA E22 400T, operating in the 410–480 MHz band. In favorable conditions, it offers a range of several tens of kilometers and reliable operation in semi-urban terrain. Transmission power and data rate can be dynamically adjusted for range or energy savings. Reed-Solomon error correction is implemented in software to improve reliability under poor radio conditions.
The terminal can act as a repeater, bridging two areas that cannot directly communicate. Messages are sent in fixed-length frames. The first frame includes source and destination addresses, optional GPS data, and 48 message characters. A second frame can carry 112 additional characters. GPS navigation tools allow users to compute distance and azimuth to any received coordinate, and also to compare multiple saved locations.
Cryptographic Security: a modern take on the “Red Phone” model
This terminal borrows its strategy from a historic system—the Cold War "Red Phone" between the US and USSR, which used one-time pad encryption with keys as long as the messages themselves, then physically destroyed. No mathematical complexity—just complete non-repeatability and zero persistence.
Similarly, this device uses a massive preloaded key sequence stored on an SD card. Keys are selected based on time—one every two minutes—synchronized using GPS or RTC. There is never a need to exchange keys over the air.
Each key is valid for two minutes only, used to encrypt or decrypt traffic during that window via AES-256 in CBC mode, and then destroyed. The system self-purges over time—past keys are overwritten as time moves forward. Even if the device is physically captured, previously used keys are already unrecoverable.
This is not theoretical: storing 256-byte keys at two-minute intervals results in just 180 KB per day. A 4 GB SD card holds over 60 years of unique keys. This model makes the communications not just hard—but mathematically and physically impossible to decrypt after the fact. The strength of the system lies not in cryptographic tricks, but in abundant storage, strict time-based synchronization, and permanent key destruction.
A Post-Apocalyptic Demonstration
To ground this project in a visually striking and symbolic context, this is a demonstration video set in a post-apocalyptic environment—a world of collapsed infrastructure, solitude, and silence on the airwaves. The terminal could be a tool of resilience, a device capable of secure communication when all else has failed....
This is not a prototype or a speculative concept. It’s a fully operational, self-contained system designed for real-world off-grid communication—without network dependencies or unnecessary software layers.
Not for commercial use – © Selva Systems – Contact for license